# Oauth SSO client for GLPI

This plugins allows user login and import from external services.
Currently connect to:
* [Google](https://developers.google.com/identity/sign-in/web/sign-in)
* [Facebook](https://developers.facebook.com/apps/)
* [Github](https://github.com/settings/developers)
* [Amazon](https://developer.amazon.com/fr/blogs/appstore/post/Tx3NJ8243NI3ONM/announcing-login-with-amazon-an-authentication-service-to-securely-connect-with-amazon-customers)
* [Azure active Directory](https://docs.microsoft.com/en-us/azure/app-service/configure-authentication-provider-aad)
* [Microsoft](https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-v2-protocols)
* [Gitlab](https://docs.gitlab.com/ee/api/oauth2.html)
* [Keycloak](https://www.keycloak.org/docs/latest/server_admin/#_oidc_clients)
* [Okta](https://help.okta.com/en-us/Content/Topics/Apps/Apps_App_Integration_Wizard_OIDC.htm)
* [OpenIDConnect](https://openid.net/connect/)
* [Apple](https://developer.apple.com/documentation/devicemanagement/implementing-the-oauth2-authentication-user-enrollment-flow)
## Setup
### Configure SSO fields
The plugin uses the external authentication feature of GLPI.
So in order to be functional, it needs some setup.
Set the fields in `Setup > Authentication > Others authentication methods` like this screenshot:
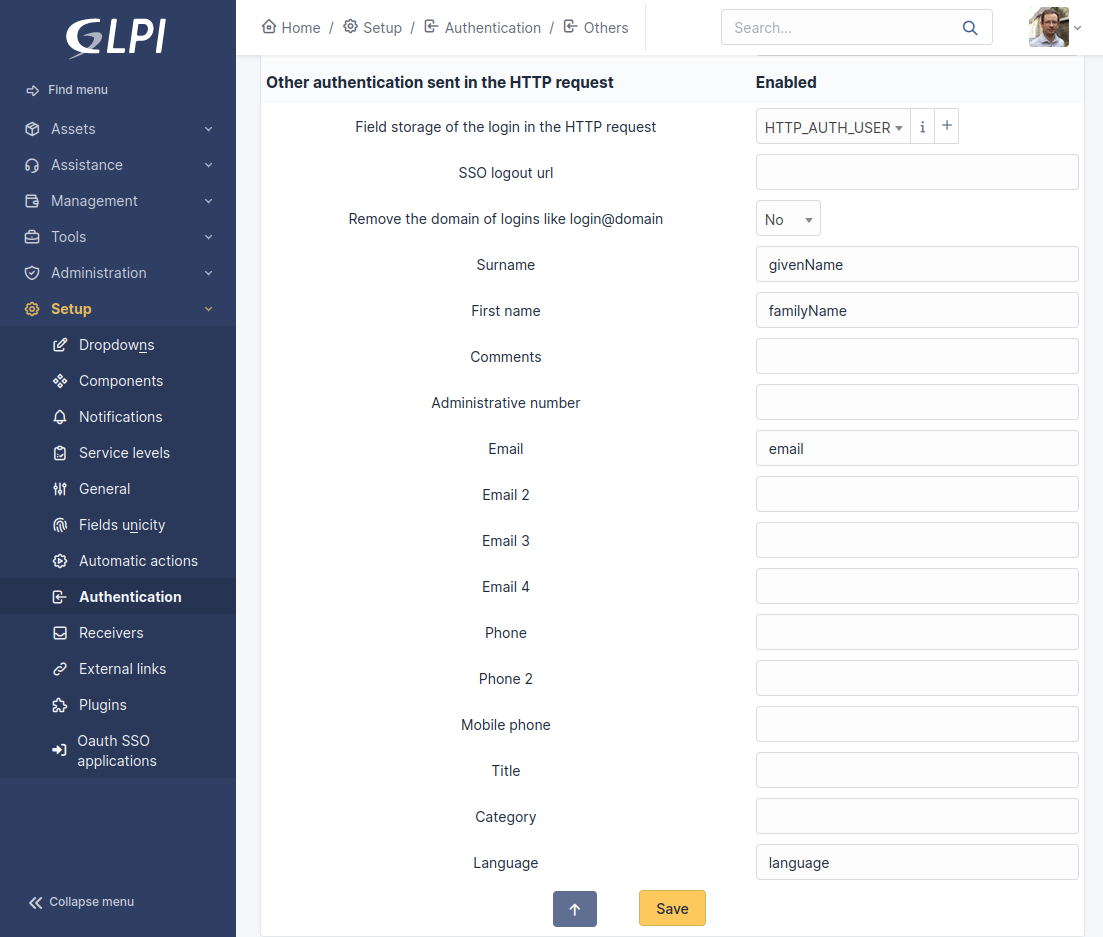
In resume, mandatory setting:
- `Field storage of the login in the HTTP request`: must be set (no matter the value)
Optionally, if you want to import unknown users you can also set:
- Surname: `givenName`
- First name: `familyName`
- Email: `email`
- Language: `language`
Also, you need to enable this import behavior of GLPI.
See in `Setup > Authentication > Setup`, the `Automatically add users from an external authentication source` field.
**WARNING**
The field 'Remove the domain of logins like login@domain' shoud be set to 'No'.
Example for google suite, if you have an email like `username@domain` and the option set to yes, the imported user in GLPI will be name `username`.
If an external person try to connect with an email like `username@antoherdomain`, it will authenticated to GLPI like it was the first email.
### Enable a login provider
The process is pretty the same for each source:
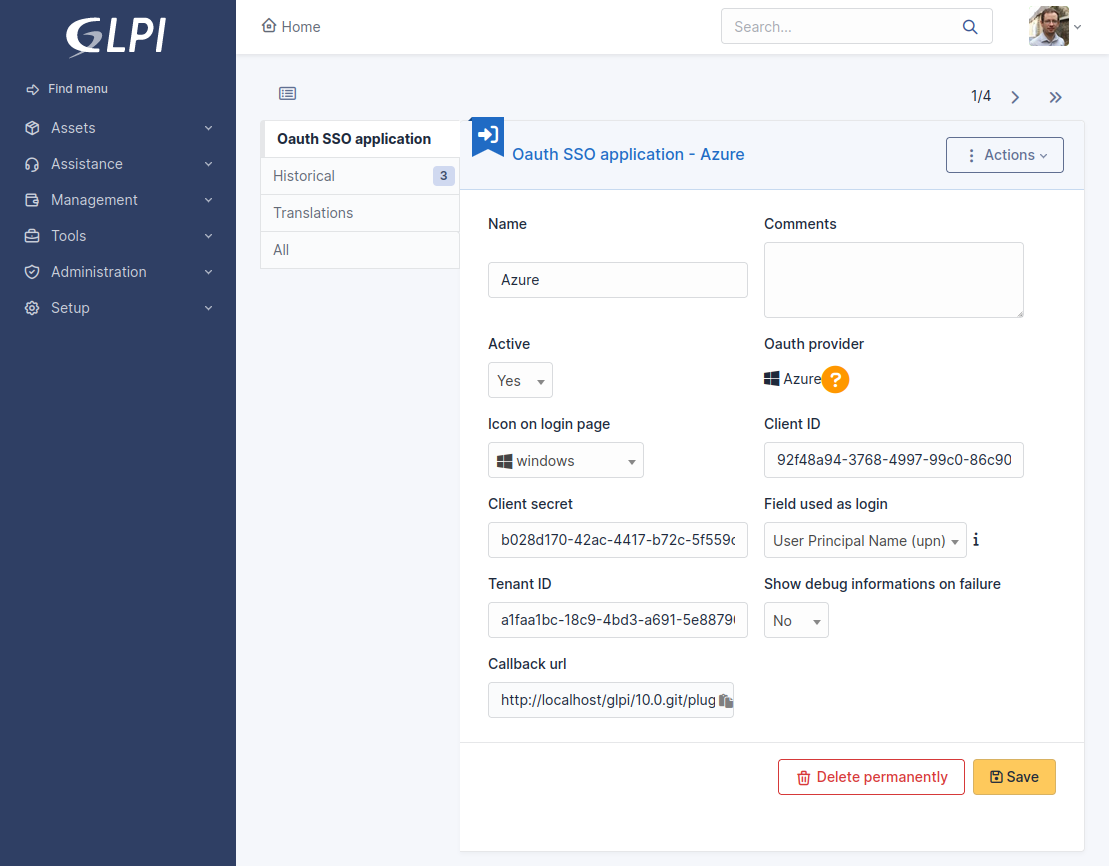
- Register an external application on service provider management console;
- Create an item in `Setup > Dropdowns > Oauth SSO applications` using `id` and `secret` of your provider application;
- Copy callback url from the plugin configuration and fill it in the console (GLPI will be called back after login on provider);
- For some providers, you need to restrict usage of Oauth api to allowed url. The filtering may also be managed by the callback url.
## Import from oauth plugin
If you previously used the `oauth` plugin, the installation process will transform its configuration into `Oauth SSO applications` automatically.
You just have to remove the old `oauth` plugin directory from your server.
## Candidates for future providers
See:
* http://oauth2-client.thephpleague.com/providers/league/
* http://oauth2-client.thephpleague.com/providers/thirdparty/
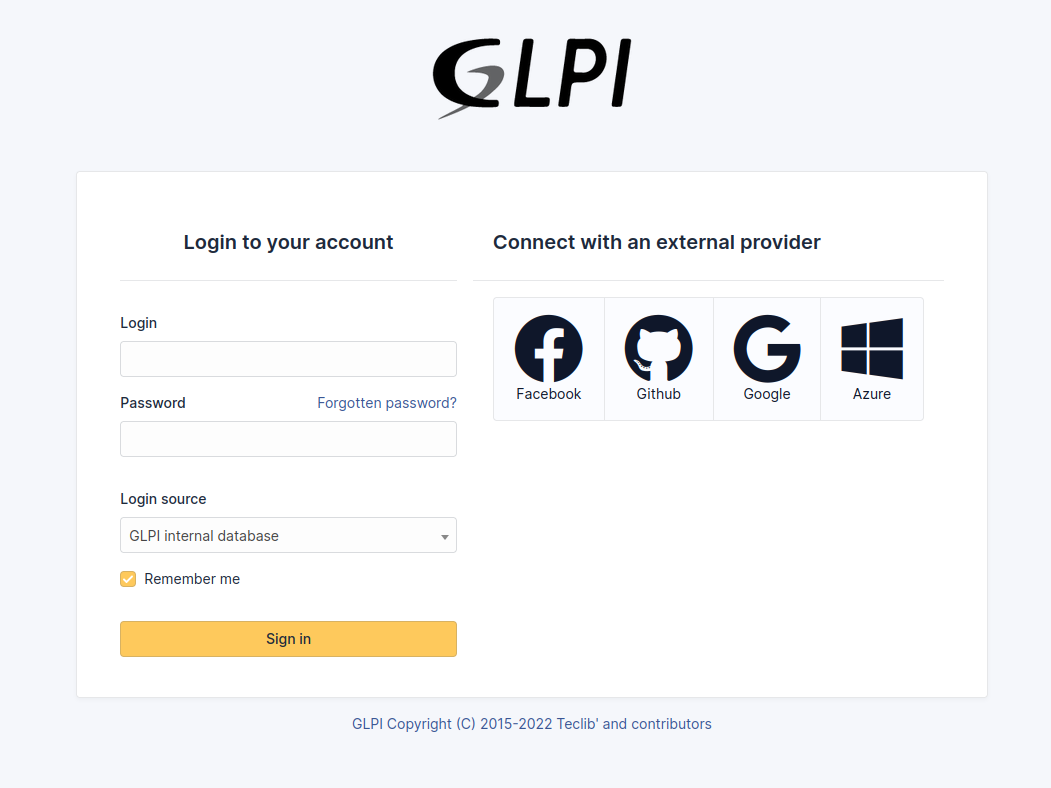
## Screenshots
[[toc]]